We’ve all been there.
I’ve seen this but with a final message of “Sorry, that password is already in use by user about2getOwned@gmail.com.”
- Login to their account
- Change their password to something else
- Set your password
But what if the password you want to set is already in use?
Refer to my above comment until that is no longer the case.
For those wanting to play this as a game, there is this wonderfully fiendish website.
https://neal.fun/password-game/
Rule 13 Your password must include the current phase of the moon as an emoji.
I got stuck on the chess one. Used to think I was pretty decent at the game. After a few tries I gave up and tried a few websites that claim to be able to solve it and none found the “correct” move.
“Chessify” on Android worked for me (also has the advantage that you just take a picture, instead of setting up the position by hand). Unfortunately 1 minute later the game gave me a chicken that I had to keep fed with worm emojis, so I created a stockpile of worms for the chicken and it died of overfeeding. I rage quit the game on the spot.
“Sorry, that password is already in use” ruins it for me. That’s not a realistic message to receive.
Maybe “Your password cannot be one you’ve used previously”.
It shouldn’t be.
But it is.
It follows the vein of some of the password rules and feedback reducing security itself. Like why disallow any characters or set a maximum password length in double digits? If you’re storing a hash of the password, the hash function can handle arbitrary length strings filled with arbitrary characters. They run on files, so even null characters need to work. If you do one hash on the client’s side and another one on the server, then all the extra computational power needed for a ridiculously long password will be done by the client’s computer.
And I bet at least one site has used the error message “that password is already in use by <account>” before someone else in the dev team said, “hang on, what?”.
It’s true, most of these rules are harmful, but also most are in common use and accepted, for some reason. I have heard of a password system that had that warning, perhaps even the account, but it was in a softwaregore screenshot context.
Should say by who. :)
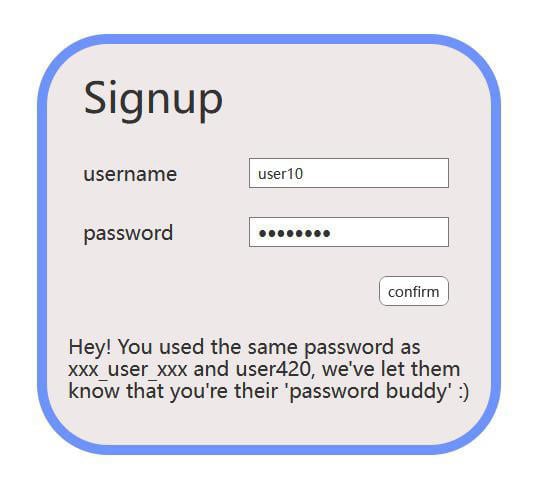
Now we are talking :)
Should be: “your password cannot be one of your last 24 passwords”
Yeah, this is important. Make it a really big number too so that I have to change my password lots of times in a row in order to put it back to what it was. ;)
Especially for those places that want your password changed every two weeks.
If they want to play that game - the calendar date becomes part of the password. It’s never the same, but you can always work it out!
Or just append a letter that increments every time you change your password, and keep a note of what the current letter is.
Passworda
Passwordb
Passwordc
…When your z password expires, just wrap back around to a.
Sorry, that password is already in use
BIG red flag. Abort. Abort.
Also I love when they only support certain special characters. So the psuedo random noise created by my password generator won’t work until I curate out the unsupported characters.
I always just refresh the password until I get a random one without the characters the randomly choose to forbid 😂
Funniest thing was when I registered on a website which parsed the \0 sequence and hence truncated the password in the background unbeknownst to me. This way you could circumvent the minimum length and creare a one character password.
Once I registered on a website. I used an auto generated password. Next time I tried to log in to the website I was confused that my stored password didn’t work. Requested to change the password, but I used the stored password again. To my surprise, it said the password must be different from the current one.
After a bit back and forth I finally figured it out. Apparently the site had a max length on the password. Any password longer than that is truncated. This truncation wasn’t applied in the login form. Only when creating a password.
I was changing my password on a pretty big company website the other day.
The password generated by my password manager kept giving me a http error (500 I think)
I generated a new password and deleted all the special characters other than the obvious ones. Boom, worked first time.
So looks like someone is not sanitising their inputs properly.
I sent them an email so hopefully they will fix.
I sent them an email so hopefully they will fix.
One can only hope. But based on my experience, they usually do not. I once sent an email to Microsoft telling them that their Microsoft account app had a vulnerability, and I even sent them the XML line they needed to add to their Android Manifest to fix it, and they wouldn’t do it because it required physical access to the device to exploit. I mean, that’s fair enough, but it was literally one line of code to plug the hole.
They eventually did add that line about 6 years later.
It boggles sometimes.
I remember about 2015 (?) In the vicinity anyway, PayPal has a 12 character MAXIMUM on their passwords.
PayPal, you know the place where you can literally transfer all the money. A 12 character MAXIMUM
I emailed them to suggest they change this requirement. And they replied saying that 12 characters was sufficient if you used special characters and numbers.
Glad they have finally changed it now.
My bank has an 8 character limit. Not minimum, limit
Password1’); DROP TABLE Passwords;–
Robert’); DROP TABLE Students;–
So is that maximum length
Looks like someone’s been playing the password game https://neal.fun/password-game/
That game made me want to punch.
A password prompt should include all criteria upfront so that you can setup your password manager to generate a fitting password.
Getting the criteria or even just partial after you entered one is fucking atrocious.
And that exact text should be available when you’re trying to log in.
Ultimately that makes it easier to break.
How many people do you suppose don’t exceed minimum requirements? Once you’ve got that you can reduce how much you need to generate.
Yeah, you can get that by going to the sign up process, but it generates an extra step that would also increase automation/scraping efforts since it’s rarely in the same place.
It wouldn’t really increase the effort much. A human would have to go through the process once, then just pass those requirements off to the script. The initial setup isn’t something you typically hand off to automation.
I know the frustration. Fucked up part is that all that crap makes it least secure not more.
Only if you write it down on a piece of paper or save it in your notes. Guaranteeing longer passwords with a variety of different symbols does make the passwords stronger though.
Password1!It’s surprising how many times I have seen this and variations.
The only one that actually reduces security is the length, as it implies it’s stored as plaintext.
The rest do improve complexity for cracking.
And that’s when they tell you what you did wrong. Sometimes they’ll reject the password without telling you why, because of some rule they didn’t list. For example, I set a password in a parking app (Flowbird) which had an unmentioned restriction against spaces and Swedish letters (dispite targeting the Swedish market). Also, it lets you set a fairly long password, but when you try to log in on their webpage they’ve set maxlength=“32” on the password field. So if you have a longer password you have to edit the DOM and remove that attribute to log in.
This already happened to me in a big service provider (electricity) website. It’s infuriating.
The worst part is that if they know that password is already in use… then they aren’t storing their passwords appropriately.
You could store the passwords as hashes and just compare the hashed value.
yes, but then they are not salted, which is what they should be doing.
But are they peppered?
True, but for the same big O they can salt the password for each user and compare it to what they have stored. My big pet peeve (that I’ve actually seen) is when they say your password is too similar to an old one. I have no idea how that could be reasonably done if they’re storing your password correctly.
Good call.
As a hamster enthusiast, I approve of each password provided by this user.
I lent my spouse’s mother our apple ID while theirs was toasted. But of course I had to change it first, since OhFuckMeH@rd3rYouFucks was finally an acceptable password for Apple but not for in-laws.
The number of times I’ve gone through that only to have it fail without explanation when I exceed the length limit - forcing me to guess if that must be the issue - is FAR higher than it should be.
And fuck any system that doesn’t provide the criteria up front.
Also fun is when the field to initially set the password is also character limited and you choose a password that’s longer than the field but don’t notice until you’ve set it and get repeated login failures afterward
Yeah that nearly makes me want to smash something when it happens. Anyone that silently truncates passwords should NOT do it, or at least truncate the creation AND login forms. Just say the limit and give a error, or handle extra input the way you’re supposed to in the enceyption algorithm and hash it to to the correct length. A length limit of say, the amount of bits the encryption key has, like 32/64/128 chracters for 256/512/1024 bit, is reasonable, any other limit is stupid.
YES, I have hit this too!
Lol, at this point just generate a password for me to save in my bitwarden.
deleted by creator
Because it’s much more fun to come up with passphrases like Correct Battery Horse Staple.
It’s a lot easier to remember that than #@?Zk23!nPw
You are not supposed to have to remember anything but your master password. :)
I’d rather try and remember than have a single point of failure for all my accounts’ security.
If the passwords are stored offline then I can’t get at them if I’m away from where they’re stored. If they’re stored online they’re not secure.
Some are online, but encrypted, with options to export the passwords in case the service goes down.
“Why should I trust them?”
Well, the software is open source, and regularly audited by people using it. Many password managers, such as Bitwarden (not sponsored, although I’d like to get a sponsorship) uses end-to-end encryption to secure the passwords so someone hacking the servers or a rogue employee can’t access anything, It would just look like random noise. You don’t have to know coding, you just have to trust that someone in the world will have the knowledge to inspect the code and report any suspicious code. Just regularly back up the passwords to a local file so you still have them in case they shut down.
Trying to remember passwords made me constantly stressed trying to remember them. A password made life much easier. Better than a single point of failure like your brain. One password is much easier to remember, and that one password can be as complex as you want, because that’s the only one you’d have to worry about.
Sincerely,
Someone who’s depressed af and constantly forget passwords
Encryption can be decrypted. A password manager encrypting your passwords is like saying your car has working brakes. It’s totally unsafe to even consider operating without but it doesn’t say much when it is there.
It’s not a matter of “why should I trust them” but “why should I trust them more than the system that already exists”. I get the appeal, but the hole is big.
If I forget a password I reset it. If I forget my manager’s password can it be reset? Is the reset option, if extent, susceptible to attack?
If an account gets compromised it could have moderate repercussions, but probably minimal depending on the account, with maybe a couple exceptions. If managed passwords get compromised that’s potentially everything. There has not, and likely never will be, an impenetrable system, so it is a possibility if not a concern.
Tacking onto this, because I mix password types too, I don’t want all my passwords in the same (even pseudorandom) style.
deleted by creator
Yeah, I switched from LastPass (after one of their many data breaches) to 1Password. I don’t know any of my passwords anymore because they’re all just generated and saved automatically. And that’s a good thing.
Because I want control of my passwords in my head not some software, it’s not like a string of random characters is any more secure than one that can actually be remembered
deleted by creator
Yes because I have an easily remembered system for a unique passphrase for any given site. Not trying to shit on password managers though, just providing a different perspective
Tons of websites reject pseudo randomly generated passwords, too
deleted by creator
That’s inherently blocking pseudo random password generators.
Max length doesn’t bother me if it’s at least 128 characters, but only allowing specific special characters is a sin.
As of last year, Wells Fargo’s passwords were even cause insensitive. Dunno if they’ve fixed it since then, but probably not
Spoken like someone who has never had to deal with corporate ‘security’ before. Password managers are great, but if your workplace has incompetent IT (e.g. probs 90% of workplaces), then you’re SOL and must play the increments game.
Is there any actual services that check if the password is already in use?
I’ve heard that some really obscure website even told you who used that exact password, because the CEO of the company owning said website complained for not having it, then the IT company who made the website had to add it. (If you ask: it was some Hungarian-owned website, and not space Karen’s 1000IQ idea)
There are definitely services that fuss if you use a password you’ve used before.
-Try to log in, password incorrect.
-Try to log in, password incorrect.
-Try to log in, password incorrect.
-Weird, ok reset password.
-“Enter new password.” Enter the password I’ve been typing the whole time. “Sorry, you can’t use your old password.”
-DAMMIT!
I’m pretty convinced this happens because their password validation isn’t responding quickly enough and it defaults to “password incorrect.”
HorseBatteryStaple
correct