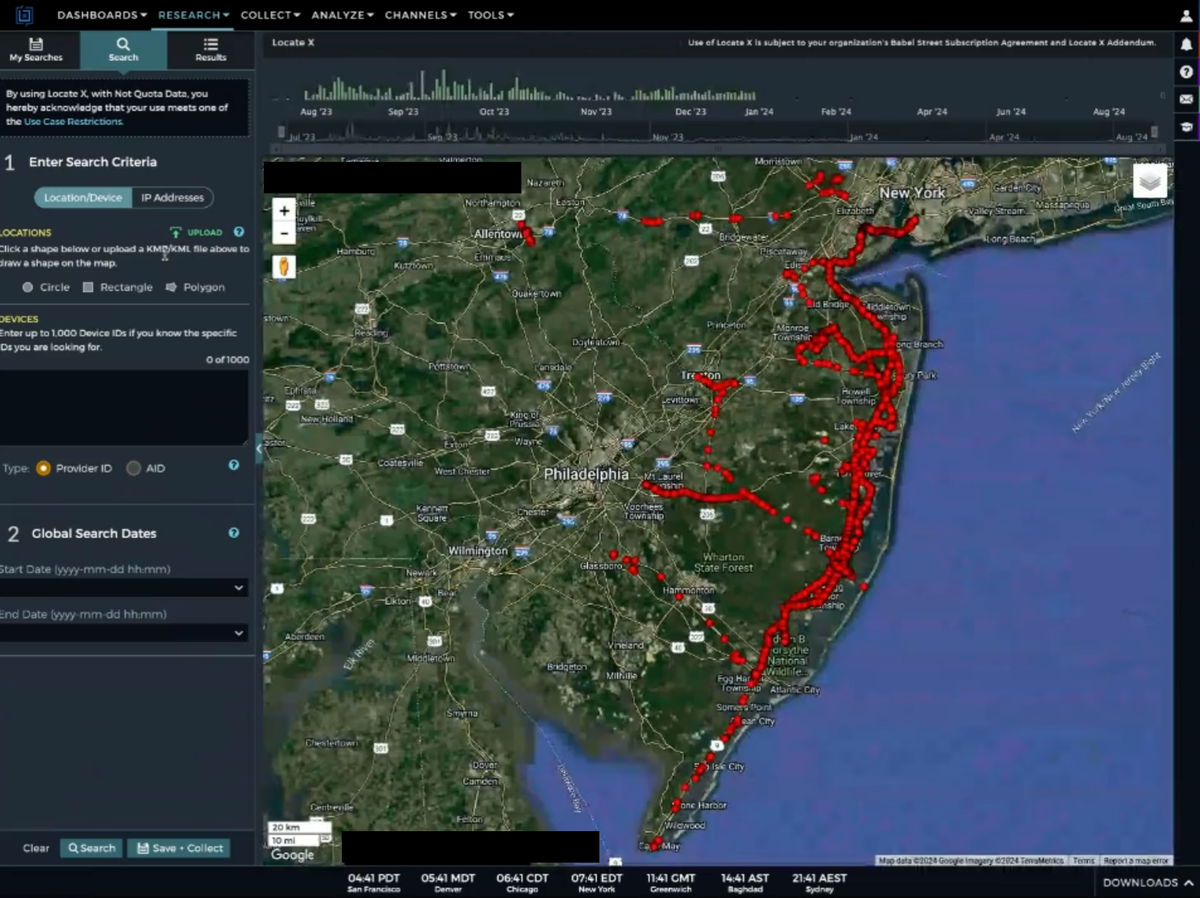
Privacy advocates got access to Locate X, a phone tracking tool which multiple U.S. agencies have bought access to, and showed me and other journalists exactly what it was capable of. Tracking a phone from one state to another to an abortion clinic. Multiple places of worship. A school. Following a likely juror to a residence. And all of this tracking is possible without a warrant, and instead just a few clicks of a mouse.


a device that constantly connects to antennas all over the place, is used to track your location.
who would have thought?
if you dont wanna get tracked - dont bring your phone.
If you don’t want to be tracked illegally, don’t bring your phone.
If you don’t want any to be tracked legally, write/call/tweet/visit your representatives.
Also just write your Supreme Court and ask them how this isn’t a flagrant violation of the intent of the fourth amendment. Seriously the founding fathers would be asking what the fuck about this. They weren’t good people but they would’ve been privacy nuts.
if you’re talking about the supreme court, as in the SCOTUS, they’re long past pretending they give the slightest fuck about the bill of rights.
Oh absolutely but it annoys them when they’re called out about it
“The fourth amendment means what we say it means” – SCOTUS, probably.
The US Supreme Court has had an antagonistic relationship to the forth and fifth amendments to the Constitution of the United States since before I was a kid in the 1970s since they often interfered with efforts to round up nonwhites. But after the 9/11 attacks and the PATRIOT ACT, SCOTUS has been shredding both amendments with carve-out exceptions.
Then Law Enforcement uses tech without revealing it in court, often lying ( parallel reconstruction ) to conceal questionable use, and the courts give them the benefit of the doubt.
Or, you know, let the gov work for you, not against you, & fully expect people to get jailed if they track you.
It’s a matter of perspective what the minimum standard should be.
Especially when a personal device like a phone is basically necessary for a normal life and even public services.
Or we could get rights protecting us from this. Especially considering that that’s a reasonable interpretation of the fourth amendment and the ninth amendment.
We already have rights protecting us from this. They aren’t being enforced.
Meanwhile when I turn off Bluetooth on my iPhone it says “for the next y hours” and there’s no option to turn it off permanently.
Don’t buy Apple?
Did you actually try looking this up. Turn it off in settings and it’s off forever until you turn it back on.
Maybe you need arch btw
Wouldn’t just keeping your phone in a metal box prevent it from communicating with anything? Keep your phone in a metal box and only take it out when you need it. Only take it out in a location that isn’t sensitive. Or hell, just make a little sleeve out of aluminum foil. Literally just wrapping your phone in aluminum foil should prevent it from connecting to anything. A tinfoil hat won’t serve as an effective Faraday cage for your brain, but fully wrapping your phone in aluminum foil should do the job. Even better, as it’s a phone, such a foil sleeve should be quite testable. Build it, put your phone in it, and try texting and calling it. If surrounded fully by a conductive material, the phone should be completely incapable of sending or receiving signals.
A Faraday cage is supposed to be grounded, so aluminum foil isn’t the same thing. Maybe you could turn the phone off, wrap it in foil, and then place it upon a conductive metal surface that is grounded, such as a 240v kitchen appliance
You could also just turn it off.
You sure it’s still not phoning home? How do you know “off” is really “off” anymore with a modern phone? It’s not like an old flip phone that you can just pop the battery out. Sure it sounds paranoid, but we’re literally talking about something that used to be the realm of crackpots and cranks - “the government is tracking all of us 24/7!” Well, it seems that’s actually literally the case now.
I absolutely do not trust that an “off” phone is actually off, unless the battery is removed (assuming it can be).
Yes. When your phone is off, it is off.
If you’re paranoid you can buy a faraday bag.
The iPhone remote locator function still works when the phone is powered off. It doesn’t work when the battery is completely dead, but it does work when the phone is supposedly “powered off.” This is irrefutable proof that iPhones at least retain some of their functions even when you’ve “turned them off.”
This is where paranoia comes into play. That’s Apple’s information. Not anyone else’s. If you believe Apple is selling it to this company and ignoring the phone setting that enables it then use the faraday bag.
But this company is not getting that information directly. It gets your information from cell tower pings at best, and social media scraping at worst.
I don’t want to encourage paranoia here but “off” does not mean “off”. Modern phones are almost never actually “powered down”. If you’re paranoid, turning your phone off is not enough. Leave it behind.
(Also a gap in your phone’s location history can also be used against you, fwiw.)
Yeah, and Alexa/Siri/Google assistant don’t eavesdrop unless you use the magic words to activate them.
There has to be some way that we could have created the architecture to do everything a phone does without letting a user be triangulated easily.
I know there is no incentive to do that, but it amazes me how far ahead the security of the web is compared to phone tech.
Like maybe if phones could authenticate without broadcasting a unique identifier. And maybe they could open a vpn style encrypted tunnel and perform their auth over that tunnel.
Idk, I know nothing about phones, but it has to be possible.
there’s the ole https://www.reddit.com/r/darknetplan/
kitschy name, but when it was established it was not even planning anything like what it is doing now. meshnet is the section you’re looking for.