Researchers from several institutes worldwide recently developed Quarks, a new, decentralized messaging network based on blockchain technology. Their proposed system could overcome the limitations of most commonly used messaging platforms, allowing users to retain control over their personal data and other information they share online.

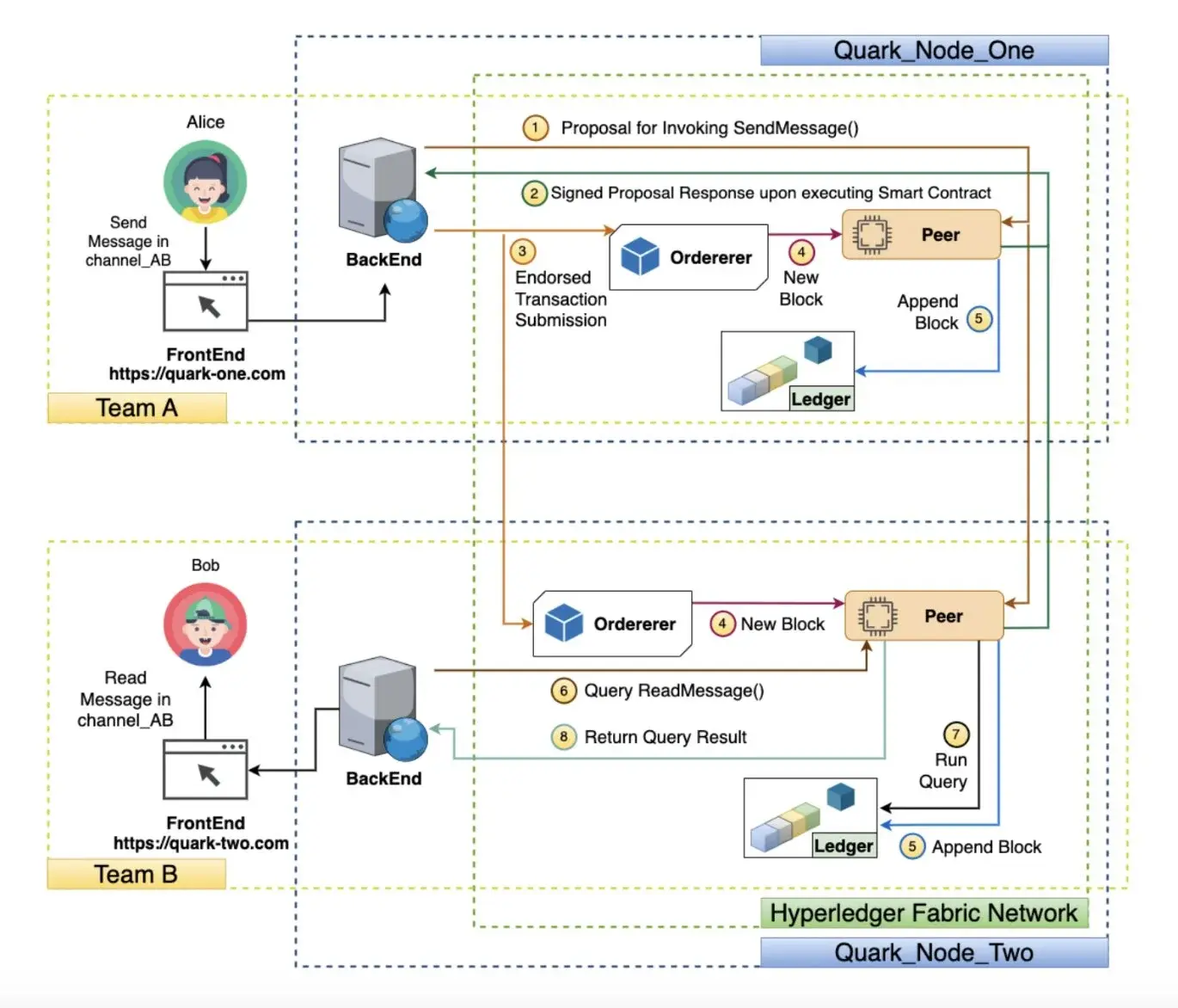
Publishing everything on a blockchain means that everybody who’s running a node has access to a copy. If confidentiality of communications is an issue, this may as well be a data breach with a few more steps. Also, how does giving everybody running a part of or monitoring the blockchain equate with “control over personal data?”
Centralized control: Only one entity can see it. Blockchain: Lots of third parties run a node, so every node can see it.
Each channel has a separate ledger: That makes surveillance of a particular communications channel much easier. Thanks. Also, each user has to have a keypair; great for pseudnonymity, lousy for repudiability.
Messages cannot be altered but they can be audited to prove their metadata. Did they learn nothing from the Obama administration? At this point in the paper I can’t shake the feeling that this is a deliberate effort to invert all of the properties of privacy.
Smart contract: Yay, more deliberately memory unsafe programming. I guess they never played with Core Wars as kids, either.
An attacker would be unable to breach the network: An attacker would just have to stand up a node. If channels are side ledgers on a blockchain, and the network assumes that nodes can come and go (which they all do, as far back as bitcoind), any node can join, say “Hey, I’d like to join this channel,” and get at the very least a pointer to the side ledger for that channel.
Long-term storage of communications is dangerous, mm’kay?
I’m not sure that’s the case, although the article is rather vague. It says:
IIUC, nodes will not have access to private keys, neither those from users nor those from channels. Users could use their keys to exchange the channel’s private key without the node getting to know it. I don’t quite understand how user’s would exchange their public keys without the node being able to play MITM, though…
Edit: Removed an irrelevant sentence from the quote
I believe their point was that even encrypted messages convey data. So if you have a record of all the encrypted messages, you can still tell who was talking, when they were talking, and approximately how much they said, even if you can’t read the messages.
If you wait until someone is gone and then loudly raid their house, you don’t need to read their messages to guess the content of what they send to people as soon as they find out. Now you know who else you want to target, despite not being able to read a single message.
This type of metadata analysis is able to reveal a lot about what’s being communicated. It’s why private communication should be ephemeral, so that only what’s directly intercepted can be scrutinized.
That was exactly why I said “Did they learn nothing from the Obama administration?”
From 2014: “We kill people based on metadata.” (Michael Hayden, former DIRNSA, 2014.ev)
There is no “harmless” here.
But in this case, the metadata is not accessible to outsiders.
If you can see it, you can analyze it. Metadata is more than message headers; traffic analysis generates usable metadata, too.
Any form of internet communication is potentially susceptible to traffic analysis, so that flaw isn’t specific to this particular design.
The goals here are to address some of the other weaknesses of communication protocols, ie lack of auditability and reliance on a central server. They do not claim it’s completely impervious to attack.
Not sure how this would work, but potentially one advantage of blockchain over peer-to-peer is less metadata needed?
All the encrypted messaged just get dumped into the public blockchain, you might be able to glean who (or at least where) a message was sent from, but the reader could be anyone with a decryption key. A bigger channel, like a newsletter type thing would just involve more read keys being available. Kind of like old school cold war numbers stations or encoded messages in the classifieds. You might be able to figure out that KGB agent Pyotr placed a classified ad for “Golden Lab, found near 5th Ave. and Main St.” in the “lost and Fond” section, but there would be no way to know which of the papers many readers would be able to decode the message.
Of course the practical problem would be the size and scale of the blockchain. I think Bitcoin 1.0 was only able to do 7 transactions/second. With each message a transaction, and each read requiring the reader to pick out their message from the pile, my above hypothesis would have to be compromised in some fashion to be usable.
Ok, so the main purpose of a blockchain is to get a bunch of computers that don’t trust each other to agree on who did what when.
A blockchain gives everyone a “voice”, so they can share what they heard. But it can’t be the sort of voice we have in the real world, because one computer can easily impersonate a million computers. In the case of Bitcoin, your “voice” is your computing power. Your computer might be able to impersonate a million computers, but your CPU cannot do the work of a million CPUs. So it is nearly impossible for single malicious computer to “drown out” all the other computers and insert a false message into the blockchain.
Bitcoin has a limit to the number of transactions per second because it wants computers to pause and talk to each other before validating a transaction. The delay is a feature, not a bug. This arbitrary limit is designed to self-adjust, so adding more computers won’t make the process go faster and removing computers won’t slow it down.
That said, computing power uses a lot of energy. Too much energy. So now there are other ways to assign voices that don’t rely on raw computing power but still prevent impersonation. This particular messaging protocol uses one of them, it is not based on computing power. But there is still a blockchain that contains everyone’s messages, and a malicious computer in theory cannot overwhelm the common consensus. So you can be pretty sure that if a message appears in the blockchain, then it was sent by the person who claims to have sent it.
Note that unlike Bitcoin, this blockchain is not public. It is not like a secret agent placing a classified ad that all can read (but not understand). Even the encrypted form of the blockchain can only be accessed by servers whose users participate in the conversation. If your server has nothing to do with a group, then you cannot glean anything at all about the conversations within the group.
Removed by mod
The ‘R’ word is a slur. Please, don’t use it here. Take a three day vacation to think about it.
Nodes can only access the blockchain for a channel if one of their users was invited into the channel. So an attacker would have to do more than just make a new node.